Build Knowledge. Digital Resilience.
Stay ahead of cyber threats and digital disruption.
Explore insights, strategies, and practical guidance from the Atelye team — empowering businesses to build true digital resilience.

Insights and strategies from the frontlines of cybersecurity, risk management, and digital resilience.
Explore practical guidance, emerging threats, and expert commentary — straight from Atelye’s vault.
Ultimate NIST CSF 2.0 Template: The Definitive Guide to Cyber Risk Management
The Complexity of Modern Cyber Security
This guide introduces the Ultimate NIST CSF 2.0 Risk Assessment Template, a comprehensive digital toolkit designed to streamline compliance, simplify cyber risk management, and empower CISOs to master all six core functions of the updated framework.
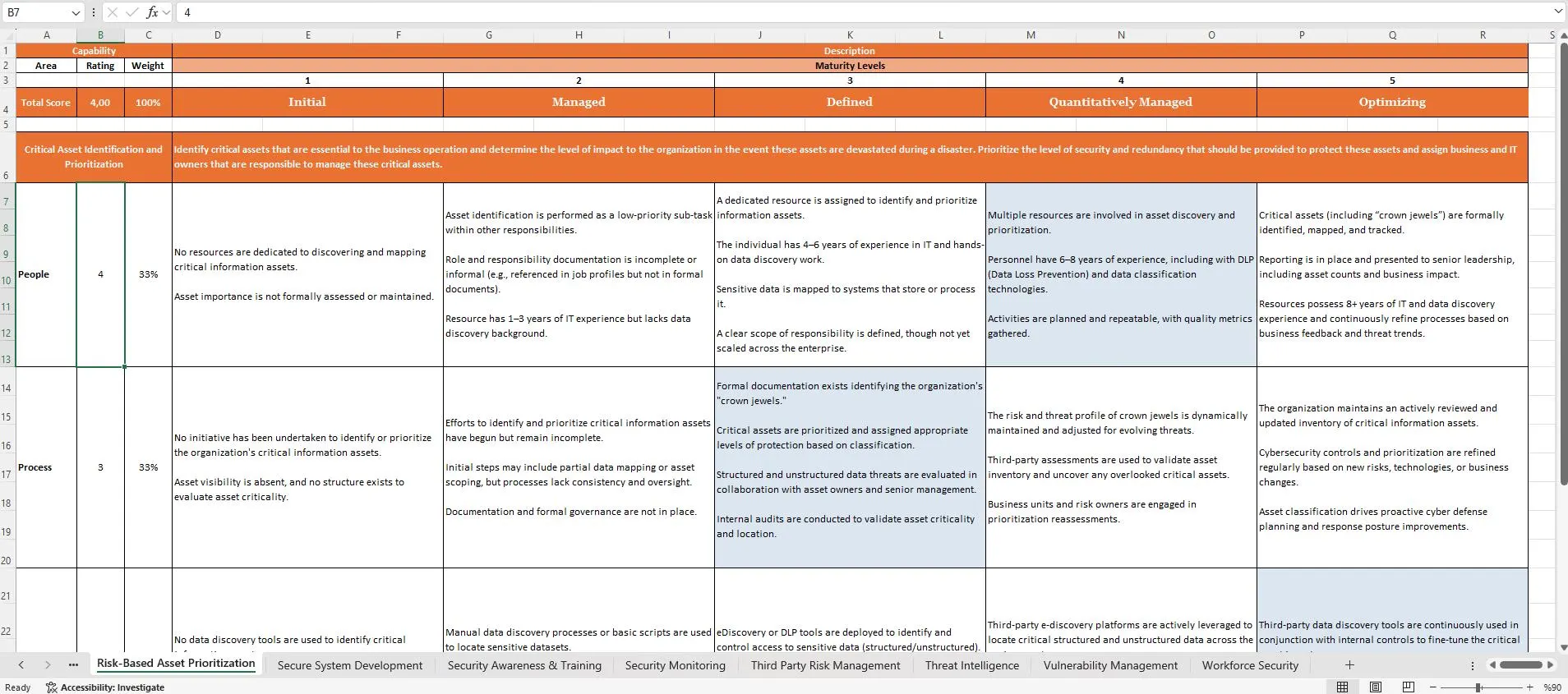
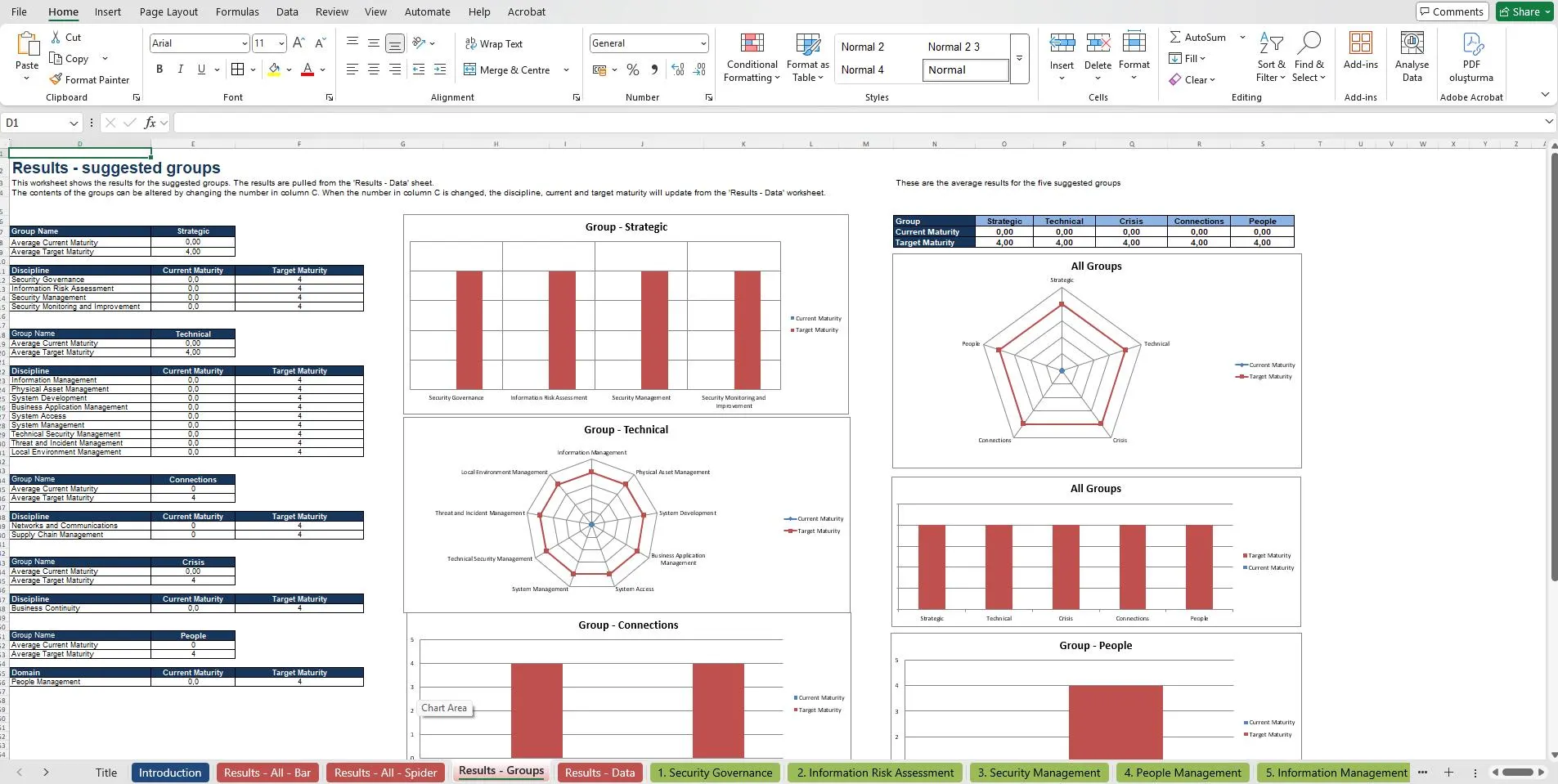
How to Measure and Improve Cybersecurity Maturity: A Complete Toolkit for GRC and Audit Teams
In today’s threat landscape, cybersecurity is no longer a reactive discipline—it’s a continuous improvement journey. Organizations of all sizes face sophisticated attacks, complex compliance requirements, and rapidly evolving technologies. Without a clear understanding of their current security posture, many businesses invest in security blindly, missing critical vulnerabilities or overspending on areas that are not a priority.
The Cybersecurity Maturity & Audit Toolkit bridges this gap. It provides a structured, repeatable, and globally recognized way to assess your current security posture, identify weaknesses, and map improvements to industry frameworks like NIST CSF, ISO/IEC 27001, and CMMI.
How to Measure and Improve Cybersecurity Maturity: A Practical Framework for GRC and Audit Teams
In today’s threat landscape, understanding your cybersecurity maturity is not a luxury—it’s a necessity. Organizations that fail to assess their security posture in a structured and consistent manner face greater risk exposure, regulatory pressure, and operational disruption.