In today’s threat landscape, understanding your cybersecurity maturity is not a luxury—it’s a necessity. Organizations that fail to assess their Information Security Maturity Model in a structured and consistent manner face greater risk exposure, regulatory pressure, and operational disruption.
This blog introduces a Practical Framework and adaptable Security Maturity Model designed for enterprises, financial institutions, and IT governance professionals.
Based on international standards and Practical Framework;
- ISO/IEC 27001,
- NIST Cybersecurity Framework,
- COBIT 5,
- ISF,
This approach goes beyond traditional audits—offering a continuous, measurable, and business-aligned perspective on cybersecurity.
Cybersecurity Maturity Model | ISO 27001 & NIST CSF Excel Template | Cybersecurity Audit Tool
🔍 What Is an Effective Practical Framework?
An Effective Control Framework (ECF) is a structured methodology to assess the maturity of security controls across an organization’s digital, operational, and risk domains. Originally developed within the financial services context, the model helps ensure that,
Critical security activities are not implemented.
Also managed, measured, and improved over time.
🎯 Objectives and Scope
The ECF framework is built to:
- Identify and manage cybersecurity risks through measurable maturity indicators
- Align control activities with global standards (ISO 27001, NIST CSF, ISF) and local regulations (GDPR, national directives)
- Support the creation of a sustainable GRC ecosystem that integrates security, risk, and compliance functions
It functions by allowing:
- Map controls to business impact and regulatory alignment
- Conduct gap analyses across 17 security domains
- Prioritize remediation based on criticality and maturity levels
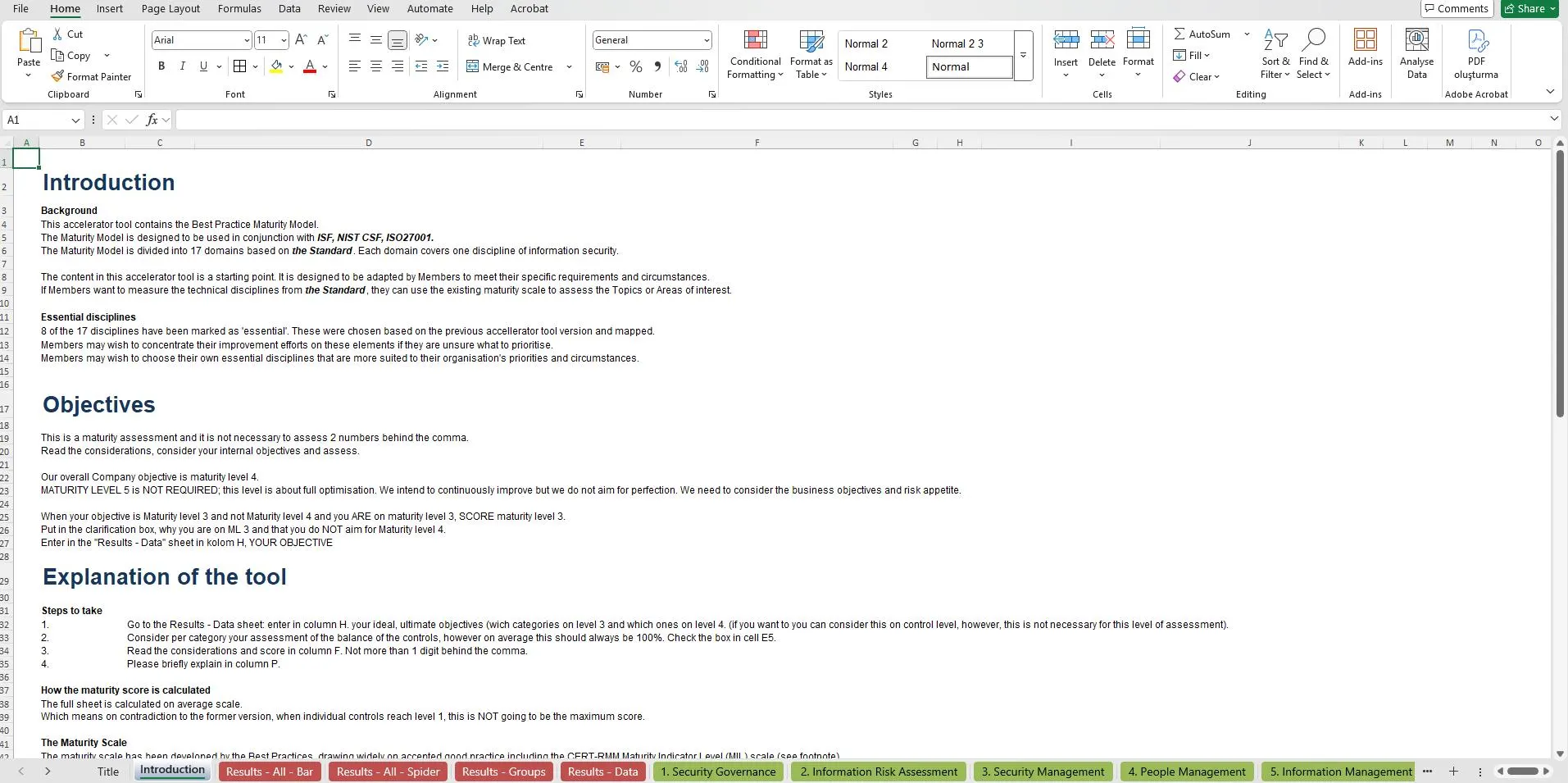
🧩 Maturity Model Structure
The ECF maturity model is divided into 17 control domains, each representing a key discipline in cybersecurity governance:
Governance & Oversight
Security Management
Information Risk Assessment
Workforce Security
Data Governance
Physical Asset Protection
System Development & Change Management
Business Application Security
Access Management
IT Operations & System Administration
Network & Communications Security
Supplier & Third-Party Risk
Technical Controls & Monitoring
Threat & Incident Management
Environmental Controls
Business Continuity & Recovery
Continuous Security Monitoring
Each domain is assessed using a maturity scale adapted from the CERT-RMM Maturity Indicator Levels (MIL):
| Level | Name | Description |
|---|---|---|
| 0 | Incomplete | No activity or documentation exists |
| 1 | Performed | Activity is conducted without standardization |
| 2 | Planned | Activity is planned and follows defined procedures |
| 3 | Managed | Resources and responsibilities are formally assigned |
| 4 | Measured | Activities are tracked, measured, and reported |
| 5 | Optimized | Continuous improvement and domain-specific tailoring |
This scalable approach enables organizations to track progress, align initiatives with business goals, and benchmark maturity across departments or units.
WHY CHOOSE US
✅ Prioritization and Focus Domains
All 17 domains are important; organizations may prioritize based on their context.
Implementation example: 11 domains were marked as “Core”:
- Security Management
- Information Risk Assessment
- Workforce Security
- Data Governance
- System Development
- Access Management
- IT Operations
- Technical Controls
- Threat & Incident Management
- Continuous Monitoring
- Governance Oversight
These represent the most immediate areas for improvement in most regulated environments.
Regulatory and Standards Alignment: Cybersecurity Maturity
The framework integrates:
ISO/IEC 27001: 2022
NIST Cybersecurity Framework
COBIT 5
ISF Standard of Good Practice
PCI DSS v4.0
Local data privacy laws
National cybersecurity guides
By mapping organizational controls to these frameworks,
How to Use the Model
- Editable and adaptable to reflect local priorities
- Aligned with organizational risk appetite
- Usable across all business units and Geographies
Example Use Cases: Cybersecurity Maturity
- A financial institution assessing its ISO 27001 readiness
- A vCISO preparing quarterly board-level maturity reports
- An audit team identifying control gaps across subsidiaries
- A consultancy delivering maturity assessments to multiple clients
To support practical implementation, organizations should perform:
Periodic reviews of strategy, control coverage, and domain-specific risks
Continuous tracking of remediation actions via a risk register
📊 Reporting & Integration with Risk Management
Cybersecurity Maturity Assessment results are recorded using a form and reviewed by Risk Management teams. Identified gaps are:
- Added to the IT Risk Register
- Assigned to responsible units
- Tracked as part of the risk and compliance programs
Results are shared with the executive to support funding decisions, regulatory reporting, and roadmap planning.

Leave a Reply