Beyond Protection:
Master Your Cybersecurity & Operational Risk with Expert Solutions
From robust information and cybersecurity frameworks to meticulous Compliance and Governance strategies, our packages empower your organization to thrive securely.
Cyber Risk Management Toolkit
Proactively manage your cybersecurity posture and stay ahead of emerging threats with our comprehensive Cyber Risk Management Toolkit. This toolkit provides the essential resources you need to identify, assess, and mitigate risks, turning potential vulnerabilities into a secure operational advantage.
Don’t let cyber threats catch you by surprise. Our framework is designed to help you build a robust defense strategy, empowering your organization to navigate the digital landscape with confidence and resilience.
Key Features:
- Integrated Risk & Vulnerability Assessments: Identify and prioritize potential weak points in your systems. Our customizable templates make risk analysis easy and efficient.
- Proactive Threat Intelligence: Stay informed about the latest cybersecurity threats and attack vectors, enabling you to build a smarter, more resilient defense.
- Incident Response Planning Guides: Get a step-by-step roadmap for handling and containing cyber incidents, minimizing damage, and ensuring a swift recovery.
Take control of your cyber risk and fortify your business against today’s and tomorrow’s threats.

Ultimate NIST CSF 2.0 Cyber Risk Assessment Toolkit | Governance, Identify, Protect, Detect, Respond, Recover Template
Master Your Cyber Security Posture with the Ultimate NIST CSF 2.0 Toolkit
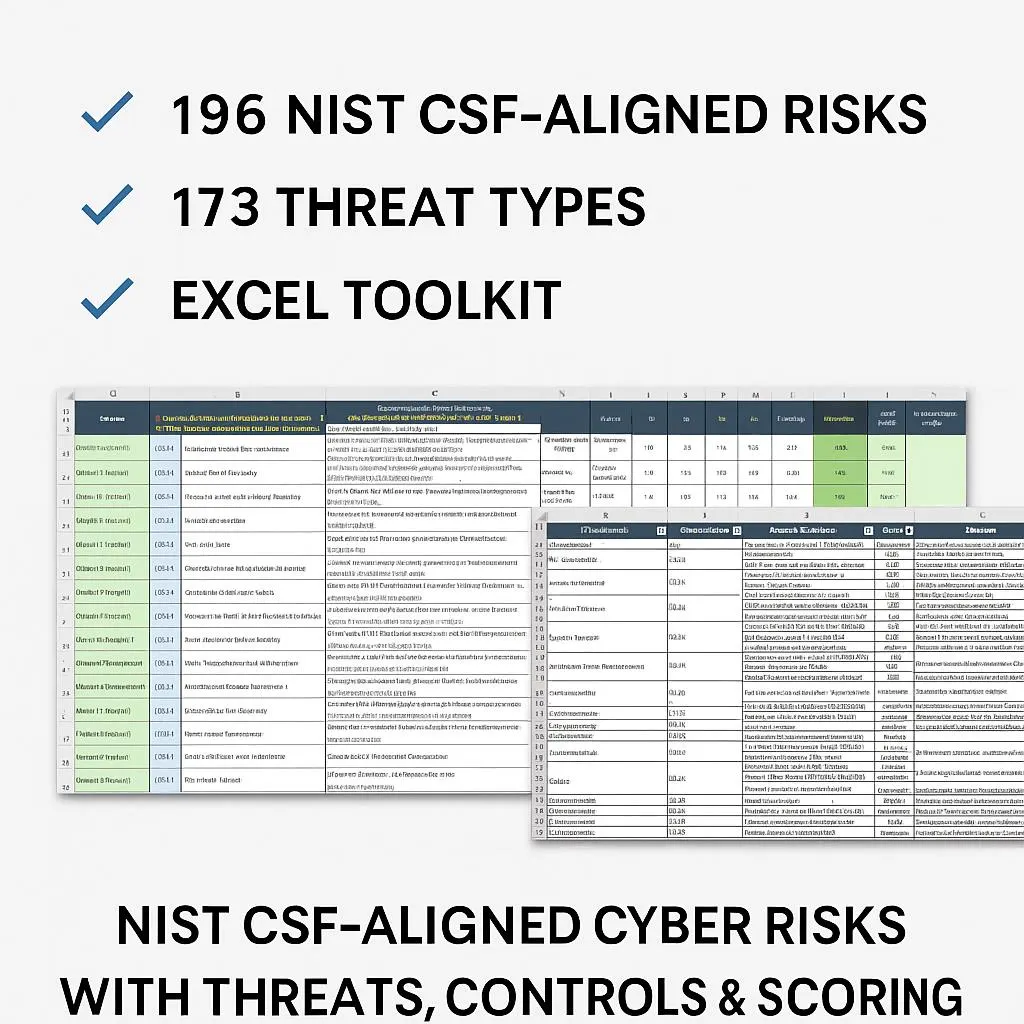
Cybersecurity Risk & Threat Catalog Toolkit
NIST – ISO 27001 Compliance Template (Excel)
Save weeks of work and be Audit-Ready with our comprehensive Cybersecurity Risk & Threat Catalog Toolkit. This professional Excel template is designed for cybersecurity professionals, GRC teams, vCISOs, and IT audit teams who need a structured, efficient, and compliance-ready risk management solution.
Our toolkit helps you navigate complex information security requirements and build a robust risk register in hours, not months. It’s fully aligned with global standards, ensuring a comprehensive assessment of cybersecurity risks.
Including NIST 800-53, ISO 27001, CIS Controls, and NIST CSF.
Showcase Features Compliance Framework
Easily navigate the complexities of data privacy with our all-in-one GDPR & Compliance Framework. This comprehensive toolkit provides the essential resources you need to build a robust Information Security and data governance program, ensuring your business is fully prepared and audit-ready.
Say goodbye to manual research and legal guesswork. Our framework is designed to help you quickly implement compliant policies and procedures, minimizing the risk of fines and building trust with your customers.
Key Features:
- Step-by-Step GDPR Checklists: Follow a clear roadmap to achieve and maintain regulatory compliance.
- Customizable Policy & Procedure Templates: Quickly establish a solid data governance foundation with professionally written documents.
- Audit-Readiness Documentation: Ensure your business is prepared for any compliance audit with easy-to-use forms and templates.
Take control of your data privacy and focus on what matters most: growing your business securely.
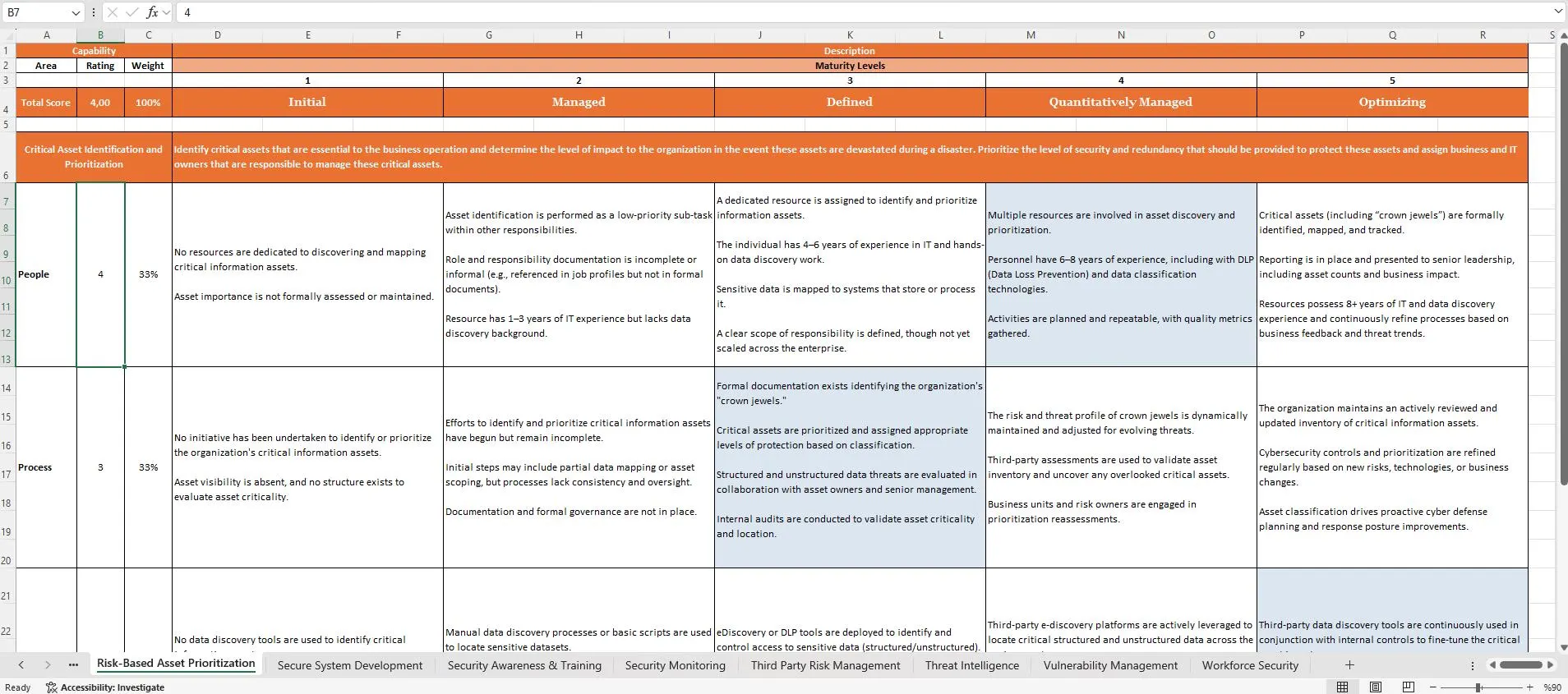
Cybersecurity Maturity Audit Toolkit
Security Assessment & Risk Management
ISO 27001, NIST, CMMI (Excel)
Cyber-resilient! Save weeks of effort with this professional Cybersecurity Maturity & Audit Toolkit. Designed for security consultants, vCISOs, and GRC teams, this powerful tool helps businesses of all sizes to perform a thorough security assessment and improve their cybersecurity posture. The toolkit is built on a proven CMMI 5 maturity model. Alsois fully aligned with global standards like ISO 27001, NIST 800-53, and NIST CSF.
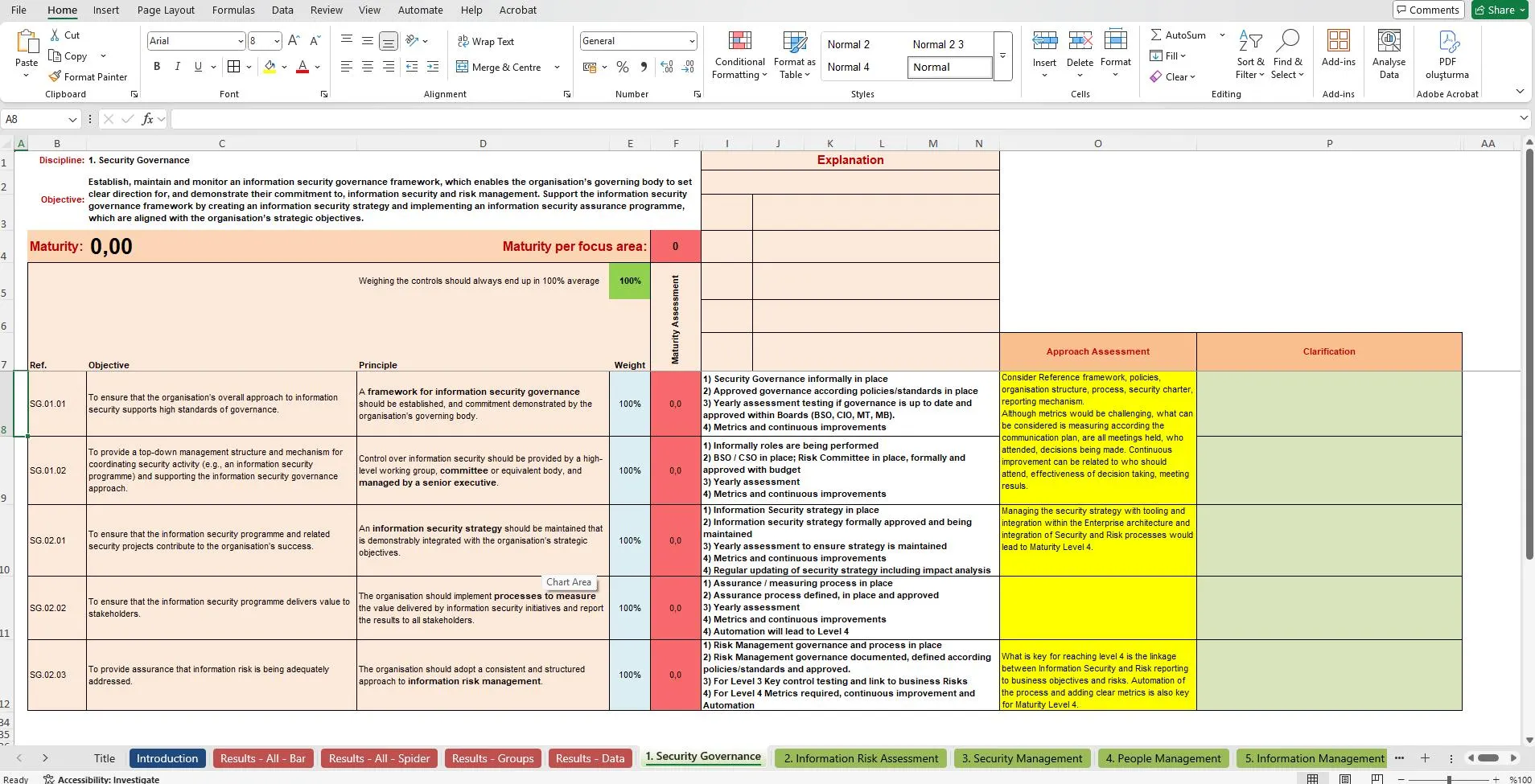
Information Security Maturity Model
ISO 27001 & NIST CSF Excel Template
Cybersecurity Audit Tool
This comprehensive Excel toolkit gives you the ultimate accelerator for assessing and improving your information security posture. We built it on an industry-proven framework, aligning fully with ISO/IEC 27001, NIST CSF, and ISF standards. You get a structured, score-based, and audit-ready framework that simplifies a complex process.

IT Internal Control Library | Comprehensive IT Governance & Risk Management Framework | Control Framework | Editable Excel Template
—More—
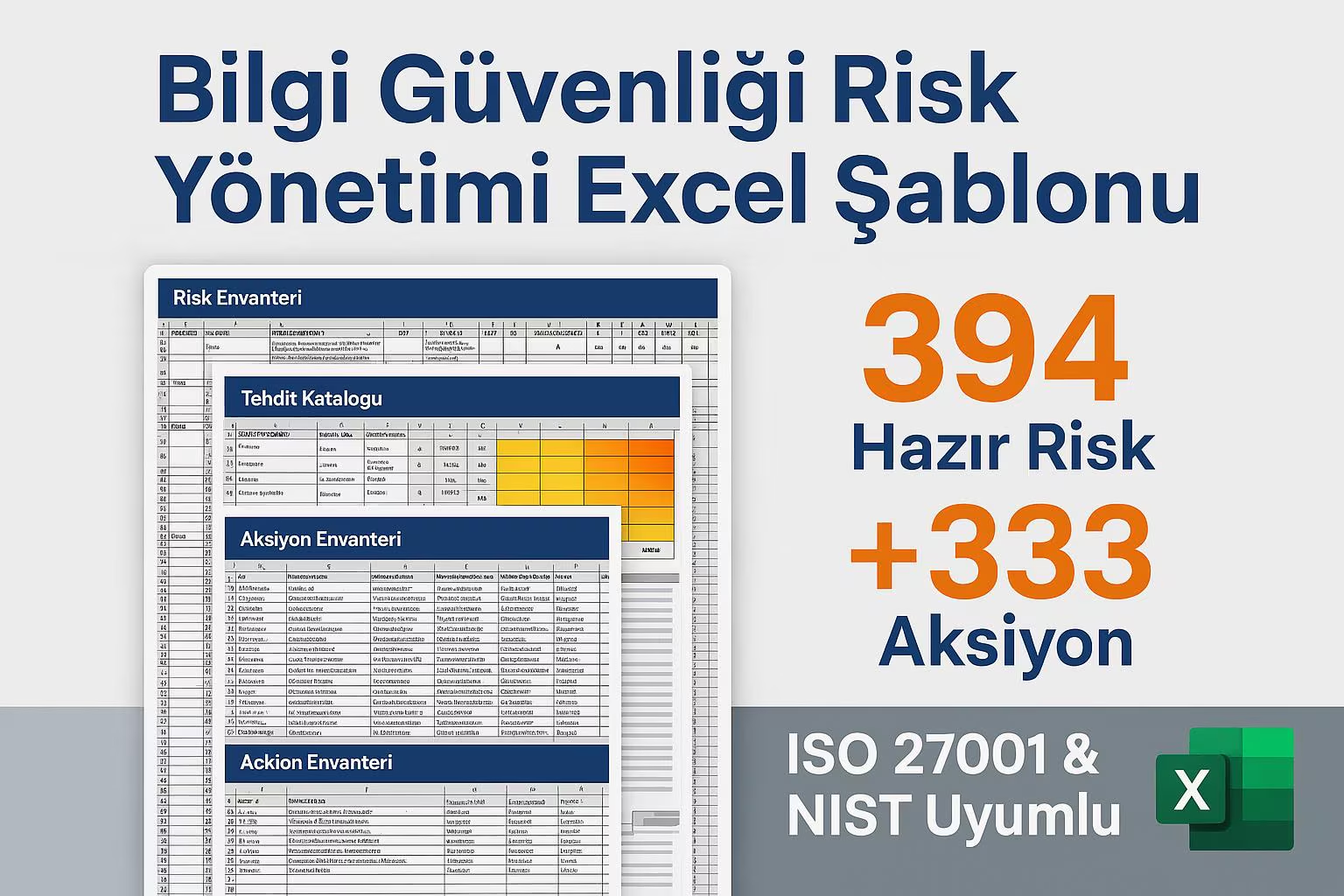
Bilgi Güvenliği Risk Yönetimi Excel Şablonu | 394 Hazır Risk + 167 Tehdit + 333 Aksiyon | ISO 27001, NIST, BDDK, Kvkk Uyumlu Türkçe Dosya
—Get—

Information Security Policy Template | Iso 27001 NIST CSF Aligned | Editable Word Format for InfoSec & GRC Use
<<Get>>
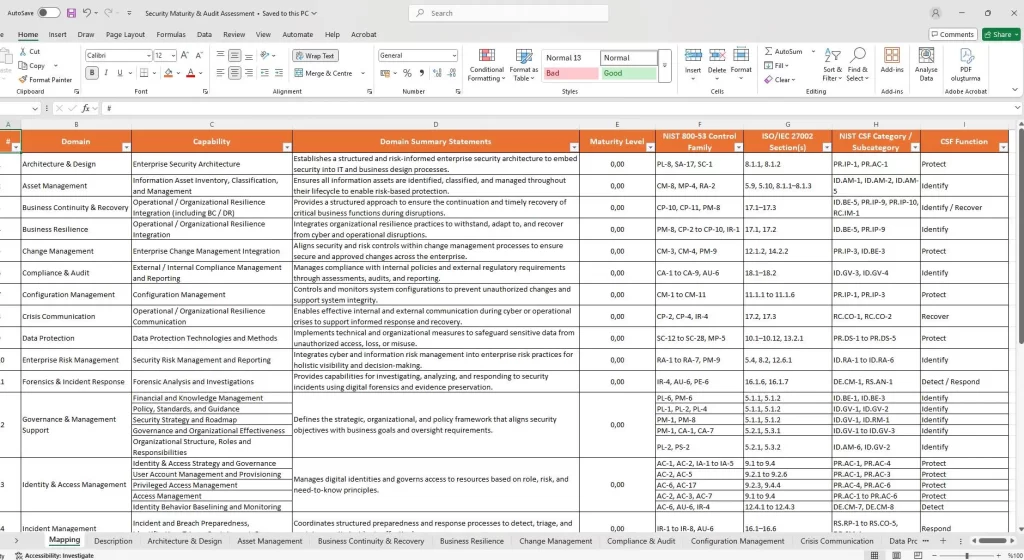
Cybersecurity Maturity & Audit Toolkit – CMMI-Based Assessment for 28 Domains (NIST, ISO 27001, CSF Aligned)

Security Control Framework Template for Auditors & Consultants | InfoSec Controls Framework with Global Standard Mapping Iso Cobit Nist, PCI DSS
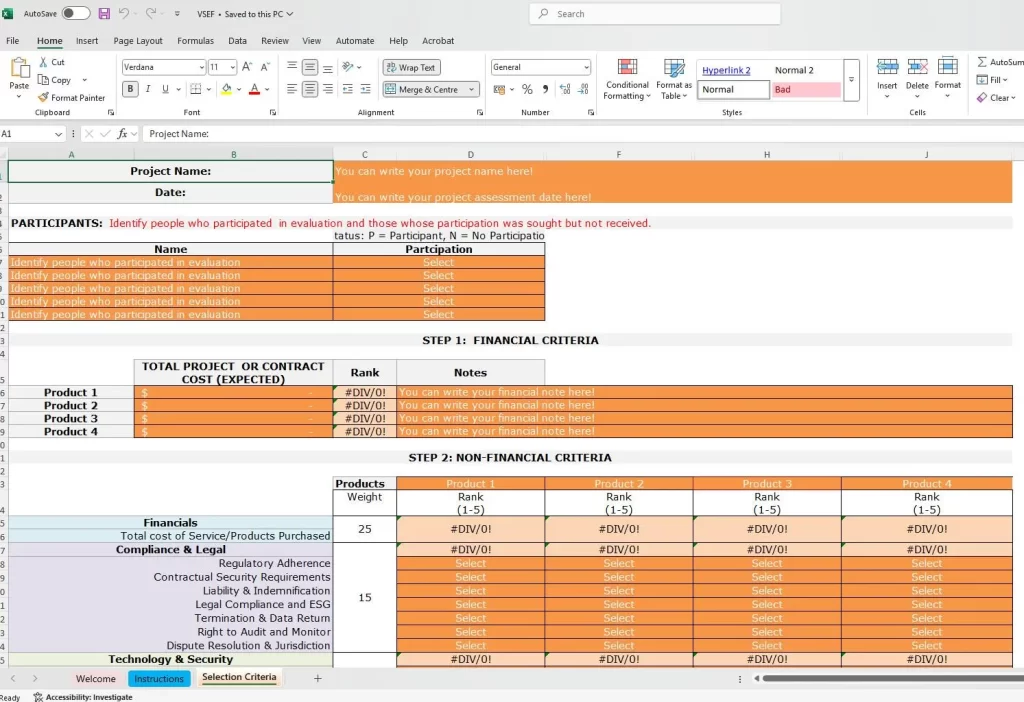
Vendor Risk Assessment Toolkit | Excel Template | ISO 27002 & NIST Csf NIST 800-53 Aligned | 3rd Party Assessment for Information Security

Information Security Awareness Training Kit – Editable PowerPoint + Posters + Canva Link| Editable Cybersecurity Presentation + Posters

CMMI-Based Cybersecurity Maturity Toolkit | 28 Domains | People-Process-Technology | ISO 27001/NIST Aligned
📥 Instant Download
Use it immediately in your organization or for client projects.
Why Our Toolkit is Your Best Solution:
✅ Achieve & Maintain Compliance: Aligned with leading global and local frameworks like ISO 27001, NIST CSF, BDDK, and KVKK, our toolkit ensures your policies and procedures meet critical regulatory standards.
✅ Flexible & Fully Editable: Get instant access to professional, editable templates in Excel, PDF, and Canva formats, allowing you to easily customize and implement solutions that fit your organization.
✅ Expert-Crafted & Vetted: Each document and guide is meticulously designed by seasoned cybersecurity and governance experts, giving you confidence in the quality and accuracy of the content.
✅ Instant, Lifetime Value: With a single purchase, you get immediate download access and a product you can use forever. No hidden fees, no recurring subscriptions—just a one-time investment for long-term security.